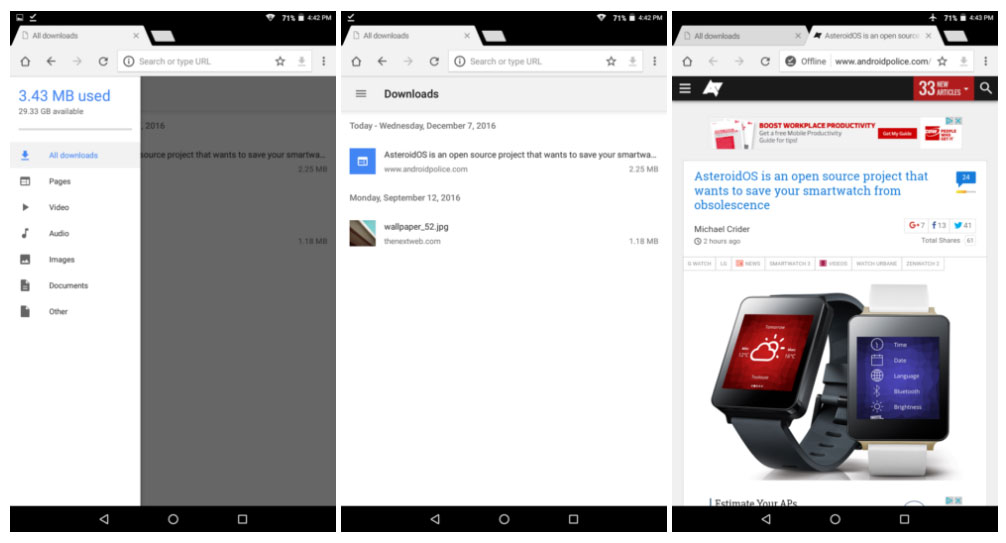
After adding support for offline videos in YouTube, similar additions in Chrome are Google’s next steps for its mobile platforms. The latest update will bring the ability to download webpages for later access, as well as a built-in Download Manager, lower memory usage and web-sharing features.
The download feature was first made available in the Chrome S5 Beta program, before arriving for everyone. The S5 update has already been released for the desktop version.
To download a webpage, you only must press a new download option, which is present at the top when you press the three dots on the side. Not only webpages, but also HTML5 videos and audios can be downloaded unless the site uses custom controls or the content is part of a stream. The content remains available offline for as long as you want, until you delete it yourself.
These changes come as a part of the new Download Manager built into Chrome for the first time, which is a move away from the conventional Android download manager.
There are new performance enhancements, as well. JavaScript is handled more efficiently, resulting in a 50-percent drop in RAM usage, followed by a feature which frees up unused zones in script after the page has loaded.
Lastly, there’s a new Web Share API, which allows webpages to instantly share content with the apps installed on your phone. There are improvements in Search and spell-checking software, as well.
Expect to see the update in an action through a rollout in the near future.